Feature Wiki
Tabs
User: Password History - Prevent early reuse of passwords
Page Overview
[Hide]1 Initial Problem
Currently (local) ILIAS users are forced to change their password on certain events, e.g. after first login (optionally), after a certain amout of time (forced due to password expiration, if enabled), etc. . Furthermore they can change their password whenever they like without being forced.
The entered/new password has to match the specified password policy criteria defined in the global user administration. Currently there is no option to prevent an early reuse of old passwords. The new password is only compared to the current password and MUST be different.
2 Conceptual Summary
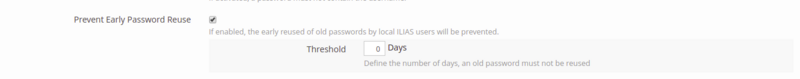
Therefore we suggest to add a new checkbox to the 'General Settings' page of the global ILIAS user administration. The label could be named 'Prevent Early Reuse of Old Passwords'. If enabled, a 'Numeric Input' appears as sub element. The administrator is able to define the amount of days as a threshold, an old password MUST NOT be reused.
The new setting does NOT affect passwords changed by administrators in the global ILIAS user administration or any kind of import (e.g. via SOAP).
3 User Interface Modifications
3.1 List of Affected Views
- Screen ID: usrf/settings/general_settings
3.2 User Interface Details
We are open for discussions about other button labels/texts.
3.3 New User Interface Concepts
None
3.4 Accessibility Implications
Nothing specific.
4 Technical Information
A password history MUST be introduced to provide the functionality described above. Therefore we need an additional database table in our SQL schema (e.g. name usr_passwd_history). This could look like:
1 | id | usr_id | hashed_pw | pw_type | ts |
- We suggest to store only a limited amount of passwords per user (e.g. 10, maybe this valued has to be configurable).
- The history has to be deleted if the user account is removed from system.
5 Privacy Information
The latest (as suggested) 10 password hashes of a local user account will be (depending on the global setting) stored in the ILIAS database. There will be now display/export of this data. The data will be deleted if the account is deleted.
6 Security Implications
On the one hand, more password hashes of a local user account will be stored in the database. On the other hand, the passwords users have to are (optionally/potentially) stronger because the latest (as suggested 10) passwords cannot be used (again).
7 Contact
- Author of the Request: Jansen, Michael [mjansen]
- Maintainer: Kergomard, Stephan [skergomard], Jansen, Michael [mjansen]
- Implementation of the feature is done by: tba
8 Funding
- …
9 Discussion
JourFixe, ILIAS [jourfixe], 12 NOV 2018 : We highly appreciate this suggestion and schedule the feature for 6.0. If enabled, the user should already be notified before entering a new password that no password should be reused that is younger than the defined threshold (e.g . 365 days).
JourFixe, ILIAS [jourfixe], 10 JUL 2023 : We like the suggestion but prefer a slighly different implementation of the feature. Instead of configuring the time until a password can be used again we prefer the option to _never reuse_ a password. This is just one checkbox and does not need additional configuration. Please adapt the request accordingly. The modified request is accepted for ILIAS 9.
10 Implementation
{The maintainer has to give a description of the final implementation and add screenshots if possible.}
Test Cases
- {Test case number linked to Testrail} : {test case title}
Approval
Approved at {date} by {user}.
Last edited: 17. Aug 2023, 13:09, Kunkel, Matthias [mkunkel]