Feature Wiki
Tabs
Cron Jobs: Require Access Control for Execution of Tasks
Page Overview
[Hide]1 Initial Problem
The ILIAS base script for the execution of cron jobs (./cron/cron.php) on the command line with PHP CLI can be executed with every valid user credentials. There is no role or permission check, so the execution is possible with even low privileges.
2 Conceptual Summary
- The ./cron/cron.php script should decorate class ilCronManager with a behaviour checking the current PHP SAPI. Only 'cli' should be a valid value here.
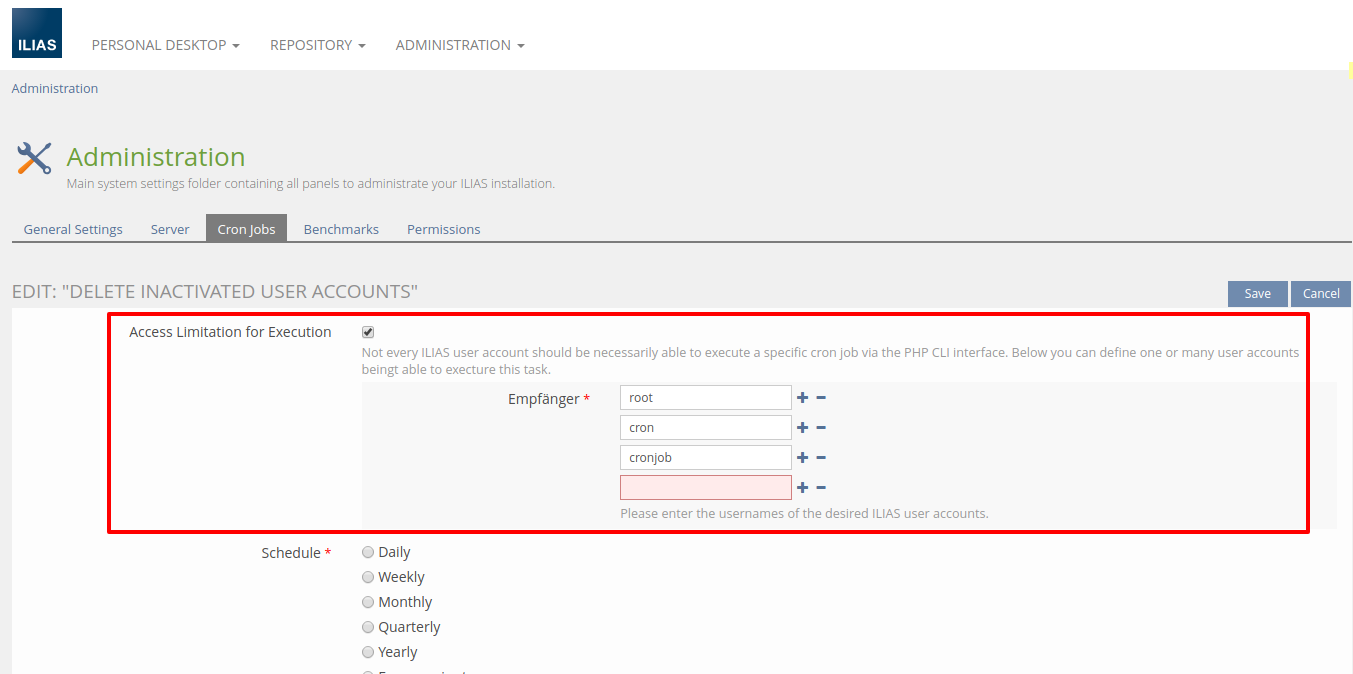
- A user with 'write' permissions (in respect of RBAC) at the 'Administration' node should be able to optionally define/configure a list of 1-N ILIAS user accounts being able to execute a specific task. If a user in an authenticated CLI context executes the cron job script and is not allowed to run a specific task, ILIAS should log this event appropriately to the global ILIAS log file.
An additional database update step could (if required) initially grant access for the 'root' user and every user matching 'cron' or 'cronjob' (case insensitive) for every existing cron job task.
3 User Interface Modifications
3.1 List of Affected Views
Screen-ID: adm/cron_jobs/ (Administration » Cron Jobs » Cron Job [XYZ] » [Edit] action (has to be supported by ervery task in future))
3.2 User Interface Details
3.3 New User Interface Concepts
None
4 Technical Information
No dependencies or relevant changes
5 Contact
- Author of the Request: Jansen, Michael [mjansen]
- Maintainer: Jansen, Michael [mjansen]
- Implementation of the feature is done by: {The maintainer must add the name of the implementing developer.}
6 Funding
- …
7 Discussion
- RBAC should be used instead of a access list to control who is allowed to run a cron job.
- We would like to have a new administration node "Cron Jobs" and WRITE permission to this administration node schould allow to run cron jobs over the web interface as well as via CLI. This node should be placed under "General Settings". Icon will be provided by ILIAS office.
Baumgartner, Robin [rbaumgartner], 18 JUN 2018: Maybe there is some reasoning behind this that i don't see, but why not drop the whole authentication/authorization in the cron context altogether? The script gets executed in a CLI environment and even if it were to be called via the web, there is hardly any harm to be done. Other similar projects even deliberately allow their cron script to be called via the web, in order to make use of external cron-like services like Webcron (e.g. ownCloud, see https://doc.owncloud.org/server/10.0/admin_manual/configuration/server/background_jobs_configuration.html).
8 Implementation
{The maintainer has to give a description of the final implementation and add screenshots if possible.}
Test Cases
- {Test case number linked to Testrail} : {test case title}
Approval
Approved at {date} by {user}.
Last edited: 18. Jun 2018, 15:12, Baumgartner, Robin [rbaumgartner]