Installation and Maintenance
LDAP authentication basics
To prepare for this configuration, you need:
- The LDAP server's URL with DNS name or IP address
- The distinguished name of the Container that holds the user accounts
- The distinguished name of the Container for group accounts, if used
- A user account that is allowed to read LDAP data and this account's password, if anonymous bind is not allowed
- A list of ilias-roles that are to be used by the LDAP users
In standard settings, login of the root user is configured to use "Default (ILIAS database)". When changing the default login method to another value, root isn't able to log in again. So before any configuration of the login methods and order, I recommend to set the root user's login method to "ILIAS databse" (without default!).
When you are not definitively sure if your configuration works, always keep a session with administrative rights in a second browser or from a different client open!
In examples we assume, that you use an Active Directory ® Domain named elearning.mycompany.local .
Users are located in Organizational Untis below the OU myusers.
Your Domain controller is named dc1.
A valid user accoung exist in an ou called functional-users below myusers, named ldap-proxy
Configuration is done on the LDAP tab of the authentication page.
The steps required are:
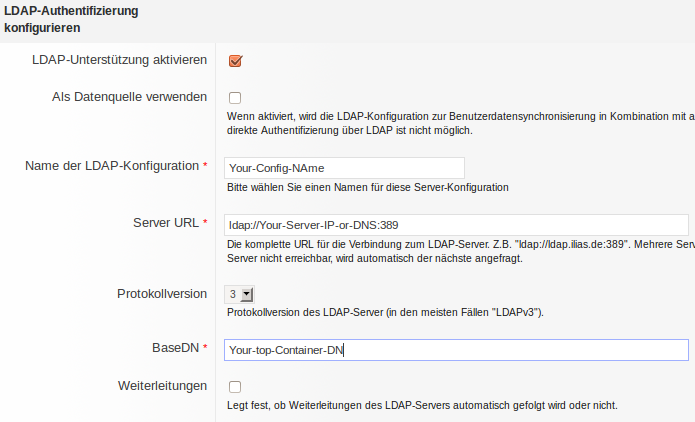
In this settings you configure basic connectivity and enable LDAP authentication. Name the configuration (this has no effect on authentication) and fill in the Server URL. Both IP and DNS name should work the standard LDAP port is 389. If the LDAP source is on a non-local net security issues have to be considered and lpaps should be used.
The BaseDN must reflect the top container that holds any objects such as users and groups. We use our Active Directory DNS Domain Name in LDAP-notification (DC=mydomain,DC=mySecondLevelDomain,DC=myTLD) in our configuration to be able to see all domain objects in our Ilias installation. Remember: LDAP uses "," as separator!
In the example you would use:
Server URL ldap://dc1.elearning.mycompany.local:389
Base DN dc=elearning,dc=mycompany,dc=local
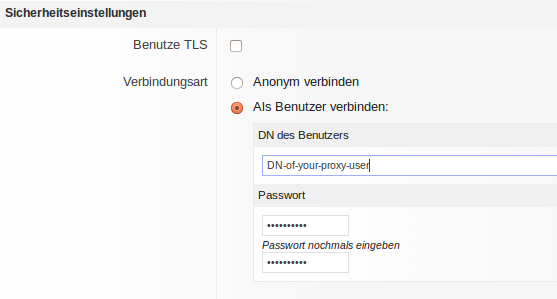
Since our LDAP Service is reached by a secured server network, TLS is not required. We have created a "LDAP-Proxy-user" who is allowed to see all Objects to authenticate to the Active Directory ® service, the complete distinguished Name (cn=Myuser,ou=Myou,DC=mydomain...) is needed here. The password must be entered twice, too.
On the Active Directory ® side the user account was created with no time restrictions, user cannot change password, no password change required as settings. Tha password must be documented but kept in a safe place, of course.
The user-login should be testet before continuing.
For the example:
cn=ldap-proxy,ou=functional-users,ou=myusers,dc=elearning,dc=mycompany,dc=local
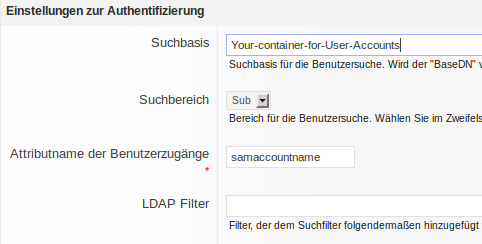
Here you need to fill in the top container holding the user accounts. Search setting "sub" tells to recursively serarch the container tree.
You have to know which attribute holds the (unique) user account name, in case of Active Directory ® this is "samaccountname". I got the advice not to use a spelling with capital an small letters.
Example:
ou=myusers
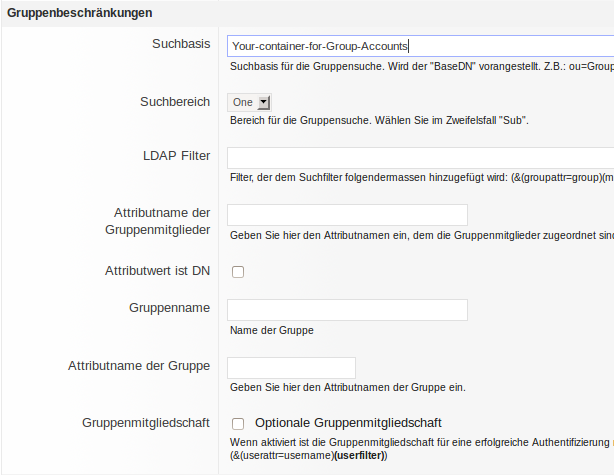
The group filter can restrict the creation of ILIAS accounts to a group membership. Use this if you have users in various containers, but not all users may use ILIAS. If you dont have requirements here you can leave everything empty.
example:
ou=mygroups
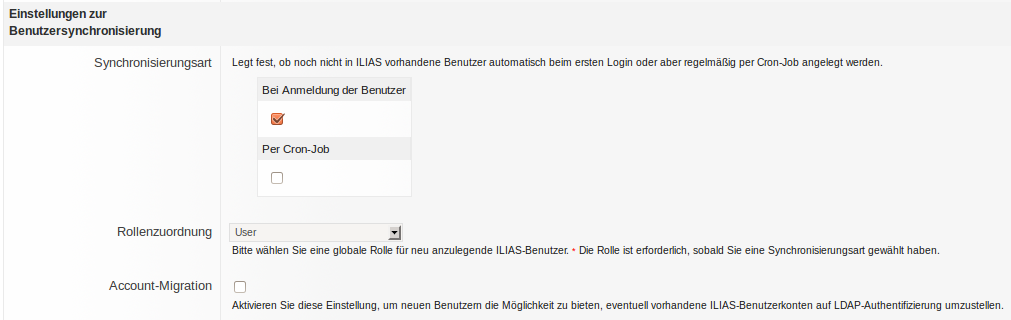
There are some design considerations for this entry:
- cron-jobs may automatically create user-accounts even if there is no login, so roles can be assigned or course- and groupmemberships created in advance.
- account creation on login avoids creation of unused accounts but requires users to login prior to assignments
After these settings are completed, switch to the authentication tab. Here you decide, if users can select their authentication method or if a fixed order of methods is used. If you use a fixed order of login methods, usually place ILIAS database behind LDAP so ILIAS tries to use LDAP before checking locally stored passwords.
LDAP queries can be used in a multi-domain environment within a forest. To bring this to work, select a domain controller working as "global catalog" an use port number 3268 instead of 389.